Publication date:2025/08/22
Imagine this: at 3 a.m., your website suddenly receives a surge of seemingly “normal” user requests. A few hours later, your accounts are being stolen in bulk, the homepage is hijacked with a phishing link, and core data just disappears... This isn’t a movie plot, but can really happen in real life.
According to the latest report by PortSwigger, HTTP/1.1, the foundational protocol that has supported the internet for over two decades, has a critical vulnerability. By utilizing it, attackers can easily bypass traditional defenses through desynchronization attacks to take over millions of websites, just like ghosts in the night. This ultimately results in data breaches, account hijacking, cache poisoning, and other severe consequences. As a result, countless websites worldwide that rely on HTTP/1.1 are currently exposed to significant risks.

Content Analysis: When the “Ghost Vulnerability” of HTTP/1.1 Meets the Real-World Attack Chain
By manipulating fields such as Content-Length and Transfer-Encoding in the HTTP/1.1 protocol, desynchronization attack makes the front-end and back-end servers have different understandings of request boundaries, thereby executing malicious operations. This is a type of HTTP request smuggling (HRS) attack, which takes advantage of an inconsistency in how the front-end and back-end servers parse HTTP requests to bypass security mechanisms through the construction of special requests.
Here are three typical cases:
- E-commerce User “Soul-Swapping” Incident
After a leading e-commerce platform was attacked, user A was able to view user B's orders and credit card information. The attacker exploited a "CL.TE" (Content-Length to Transfer-Encoding) smuggling attack to inject session hijacking code into the cache, causing user sessions to be cross-matched. Sensitive data was leaked without detection for 48 hours.
- Government Service Platform Hit by JS Malware
A municipal government service system was compromised via the ‘0.CL’ attack vector (i.e., ‘Content-Length: 0’ while actually carrying a malicious payload), which polluted the CDN cache. When users accessed the “Social Security Inquiry” page, the injected malicious script stole their login credentials, resulting in a massive leak of citizen information.
- “Ghost Transfers” in Financial Apps
The attacker launched an "Expect-based" smuggling attack on the app interface of a particular bank, exploiting this method to circumvent the API gateway's signature verification. The forged transfer requests were mistakenly recognized as legitimate instructions by the back-end server, resulting in small-amount fund thefts across multiple accounts.
In fact, due to the inherent logical flaws in the message parsing mechanism of HTTP/1.1, this application protocol, which has been widely used for 28 years, cannot defend against such attacks by simply enabling HTTPS or updating the web server.
Solutions: From Immediate Remedy to Ultimate Solution
- Immediate Remedy: Security Baseline Transformation
The risks can be temporarily mitigated by modifying the middleware configuration and leveraging the security baseline to block ambiguous requests, or disabling connection reuse between upstream and downstream services. However, this can not make the isuue completely solved and may influence the service performance.
- Ultimate Solution: Upgrade to HTTP/2
Upgrading to HTTP/2 is the ultimate solution. The binary framing mechanism of HTTP/2 clearly delineates the request boundaries, eliminating parsing ambiguities. However, not all mainstream vendors (such as Nginx, Akamai and CloudFront) support HTTP/2, which poses significant implementation challenges.
- Excellent Practice: Deploying WAF
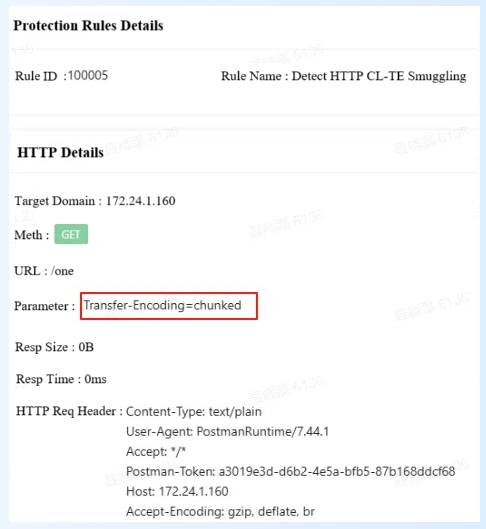
Given the complexity of HTTP/1.1 request smuggling attacks and the reality that users cannot quickly upgrade to HTTP/2, WebRAY's Web Application Firewall (RayWAF) can provide identification of and protection against multi-scenario request smuggling attacks through a set of combined rules. These scenarios include CL.TE (the Content-Length header exists, but Transfer-Encoding is chunked encoding), TE.CL (the Transfer-Encoding header exists, but Content-Length is overridden or incorrectly calculated later), and TE.TE (multiple Transfer-Encoding headers exist with conflicting values).
- Capability One: Protection Through Protocol Compliance
Real-time detection of conflicts between Content-Length and Transfer-Encoding to intercept malicious requests.
(1) Prevent CL.TE Smuggling
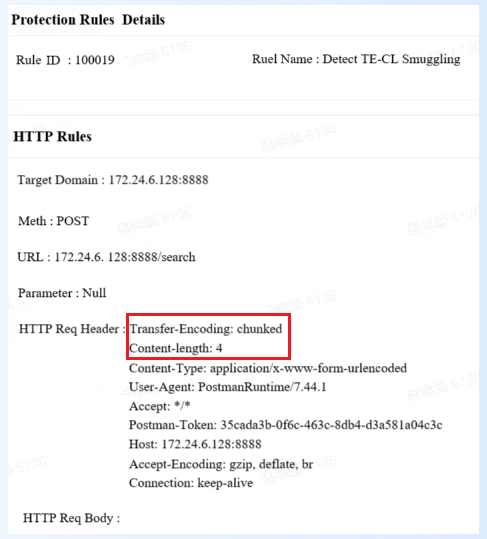
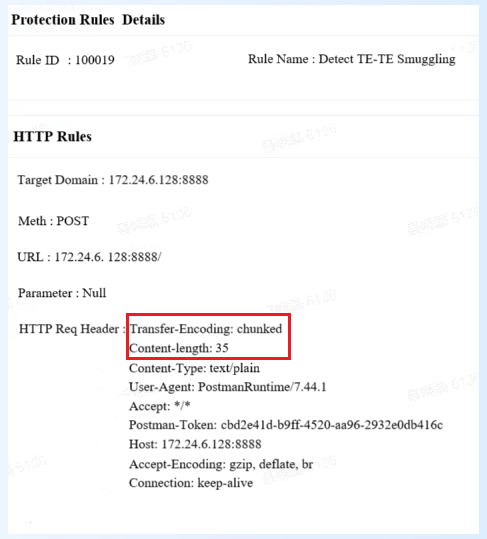
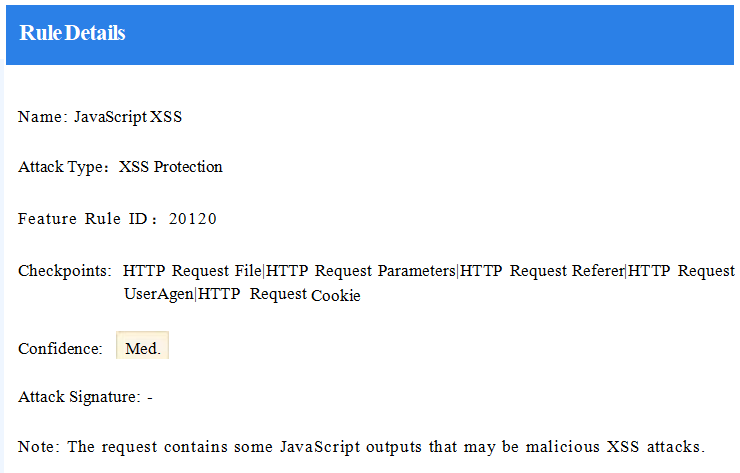
- Capability Two: Prevent Cache Pollution
- Capability Three: Protection Through HTTP/2 Compliance
Conclusion: There is No Middle Ground in Security
HTTP/1.1 will eventually be phased out, but a comprehensive upgrade cannot be achieved overnight. During this high-risk "interim period" of transition, passively waiting is the greatest risk.
About RayWAF
Intelligent Protection Redefined | RayWAF
Leveraging 15+ years of cybersecurity expertise, WebRay's RayWAF delivers enterprise-grade protection through adaptive, AI-powered defense. This multi-layered solution combines behavioral analysis, machine learning, and real-time threat prevention to effectively combat both known vulnerabilities and emerging threats—including zero-day exploits and business logic attacks—while ensuring optimal performance across cloud, hybrid, and on-premises environments.
Intelligent Semantic Protection
ML-driven semantic analysis for context-aware threat blocking with near-zero false positives
Machine Learning Protection
Real-time ML profiling of site behavior with adaptive threat detection (99.99% accuracy).
Scan Trap Protection
Decoy-based anti-crawler defense against bots and path traversal attacks.
Honeypot Dual-Mode Threat Protection
Honeypot-powered active-passive defense with attack detection and source tracing.
BOT Protection
Patented dynamic token authentication approach prevents automated attacks and transaction fraud.
Active Defense via Bypass Mirroring
Bypass deployment mode ensures business with uninterrupted security for mission-critical systems.