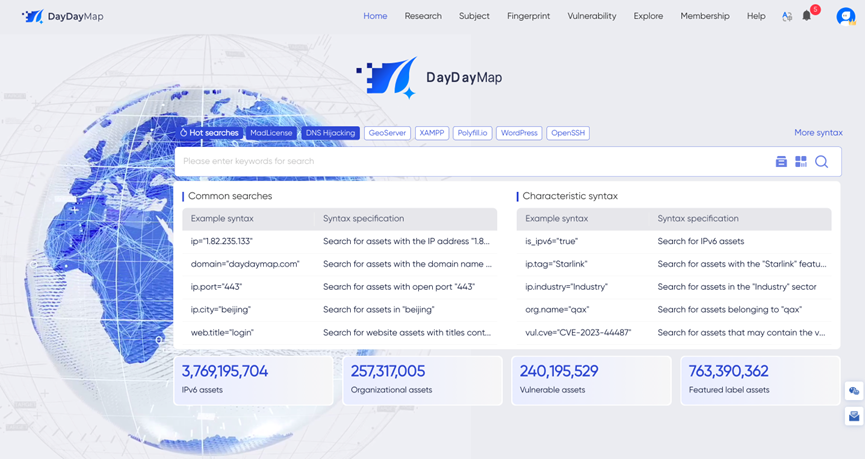
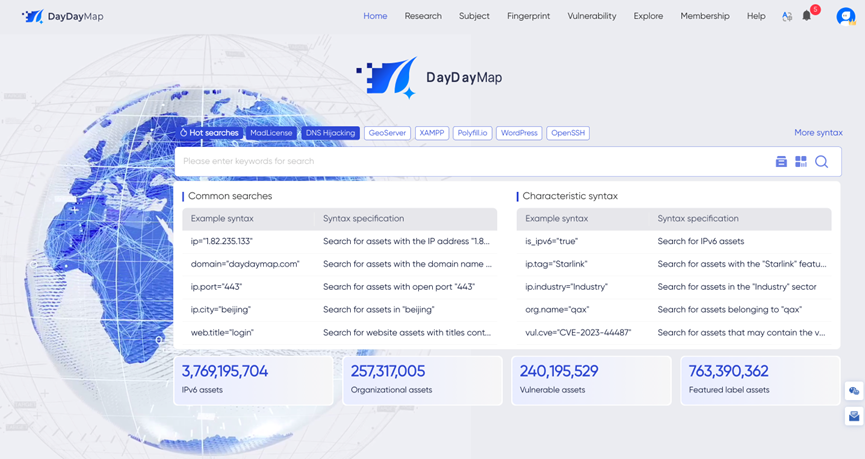
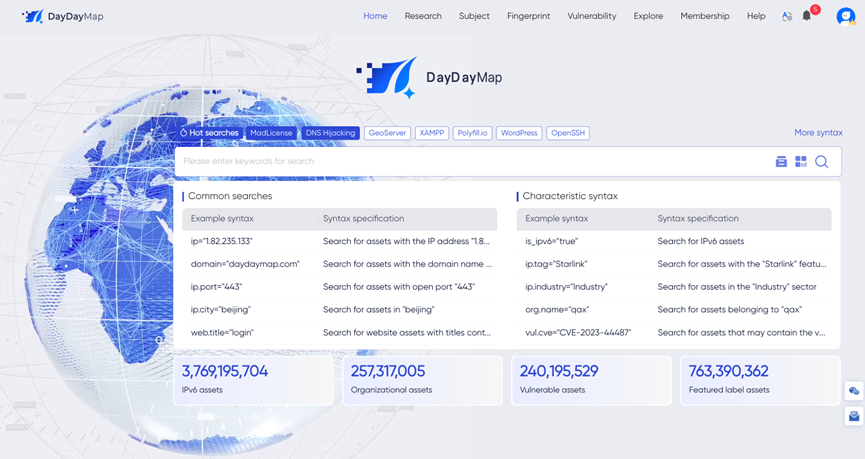
DayDayMap is a SaaS service platform that provides comprehensive, precise, and real-time global network asset mapping services.

Effortlessly discover and assess network assets, identify vulnerabilities
Contact WebRAY
-
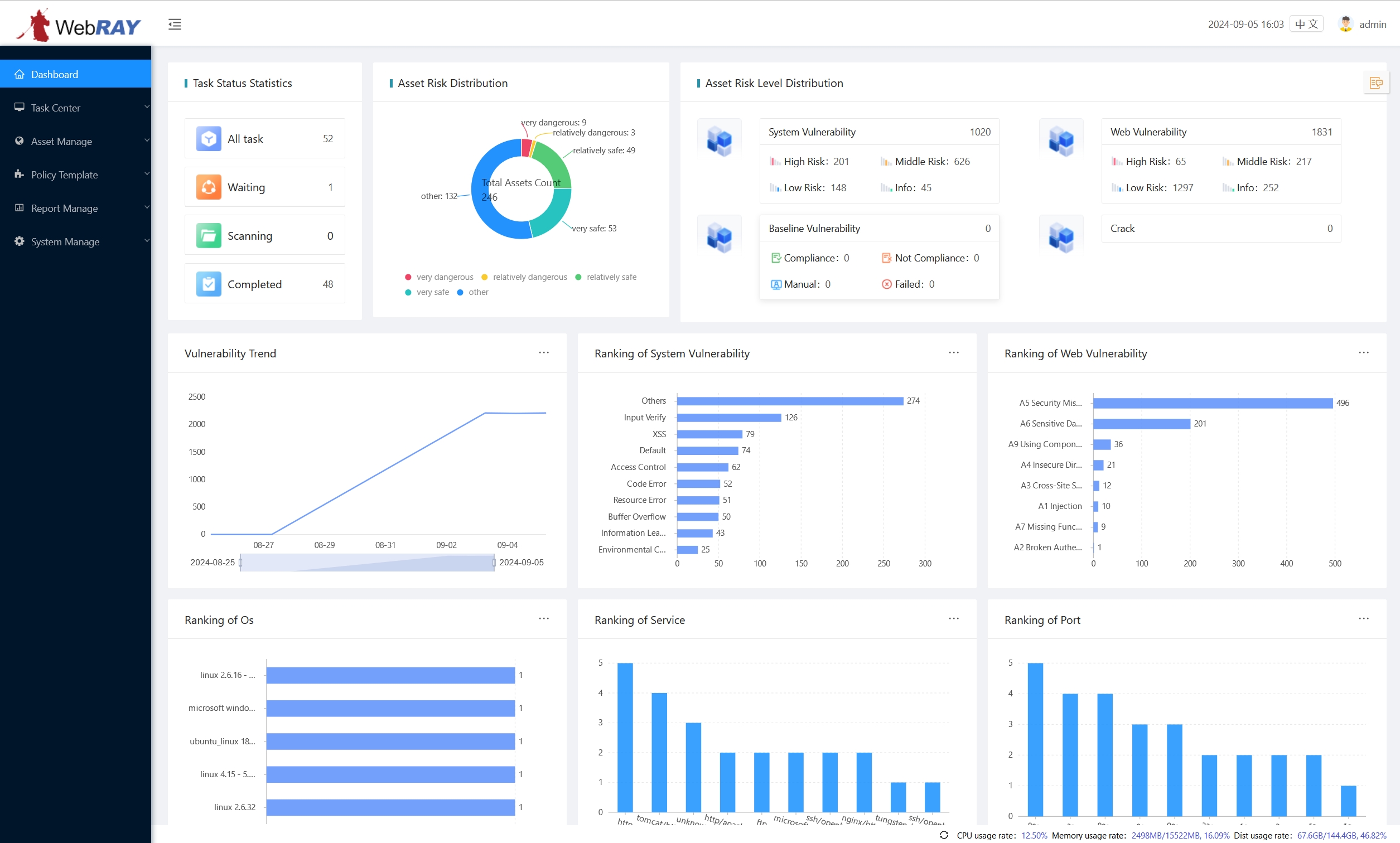
 Powerful System Vulnerability Scanning
Powerful System Vulnerability ScanningThe system conducts in-depth scans of operating systems, software applications, and hardware devices to detect various potential security vulnerabilities and risks. For operating systems, the scanning functionality can identify kernel vulnerabilities, privilege escalation flaws, and misconfigured security settings. In terms of software applications, it checks for outdated versions that may have known security vulnerabilities. This proactive approach enables clients to receive security risk assessments and remediate vulnerabilities before hackers can exploit them.
-
 Professional Web Application Vulnerability Scanning
Professional Web Application Vulnerability ScanningThe system automatically detects a variety of potential security vulnerabilities in web systems, including but not limited to SQL injection, cross-site scripting (XSS), file upload vulnerabilities, and directory traversal issues. Through comprehensive analysis of web structures and server configurations, the web scanning feature quickly and accurately identifies weak points that may be exploited by hackers.
-
 Flexible Password Guessing Functionality
Flexible Password Guessing FunctionalityThis feature attempts various combinations of potential passwords to guess user login credentials. It typically utilizes known password patterns, common password dictionaries, and user-defined combinations. During the guessing process, it can implement customized guessing strategies for different systems and applications.
-
 Comprehensive Database Scanning Capabilities
Comprehensive Database Scanning CapabilitiesThe system supports thorough inspections of various types of database systems, focusing on database configurations, authentication and authorization, as well as vulnerability and patch management to promptly discover and assess security weaknesses.
-
 Extensive Baseline Configuration Verification
Extensive Baseline Configuration VerificationThe system performs a comprehensive scan of security configuration baselines. By comparing established security standards and best practices, baseline scanning quickly and accurately identifies gaps between system configurations and security requirements.
-
 Robust Container Image Vulnerability Scanning
Robust Container Image Vulnerability ScanningThe system scans container images to uncover vulnerabilities and configuration issues before deployment, enabling security administrators to identify potential security concerns early, control the dissemination of problematic images, and formulate standard response measures.

.png)