Contact WebRAY
-
 Cost-Effectiveness and On-Demand Allocation
Cost-Effectiveness and On-Demand AllocationIt provides cloud cryptographic services with pay-as-you-go pricing. A single physical cryptographic resource pool can create multiple virtual cryptographic machines with varying performance levels, functions, and versions.
-
 High Availability and Elastic Computing
High Availability and Elastic ComputingThe cryptographic resource pool cluster provides business systems with highly available and elastic cryptographic computing services. Cryptographic modules support seamless takeover and enable dynamic allocation of cryptographic resources.
-
 Cluster Management
Cluster ManagementIt supports cluster management by seamlessly integrating with mainstream cloud management platforms and by enabling cloud-native control. The pool can be managed by the cloud platform through API calls.
-
 Diverse Cryptographic Services
Diverse Cryptographic ServicesA wide range of cryptographic services can be provided, including encryption and decryption, digital signature and verification, integrity verification, key management, timestamping, transport encryption, e-signature, and database encryption and decryption.
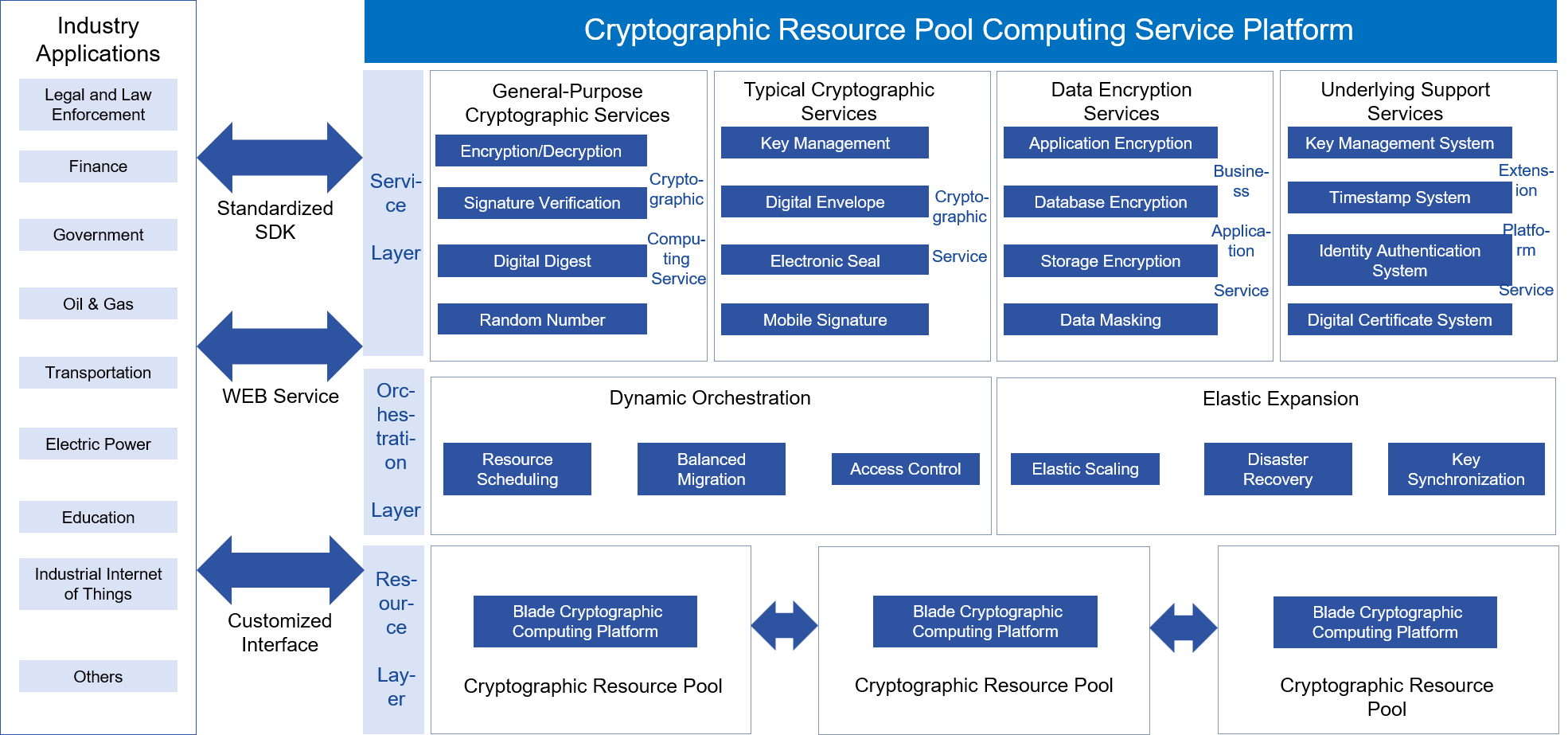
Typical Deployment
The cryptographic resource pool provides consolidated cryptographic device management, unified key management, and integrated cryptographic computing services. By providing on-demand cryptographic service, it simplifies application system integration and ensures the compliance, accuracy, and effectiveness of cryptographic applications across diverse business scenarios. This enables the rapid construction of cryptographic networks and cryptography-enabled business application infrastructures.