Products
Blog
Technical Blog is a platform offering the latest cybersecurity insights, covering recent threats, new defense strategies, popular security concepts, and so on.

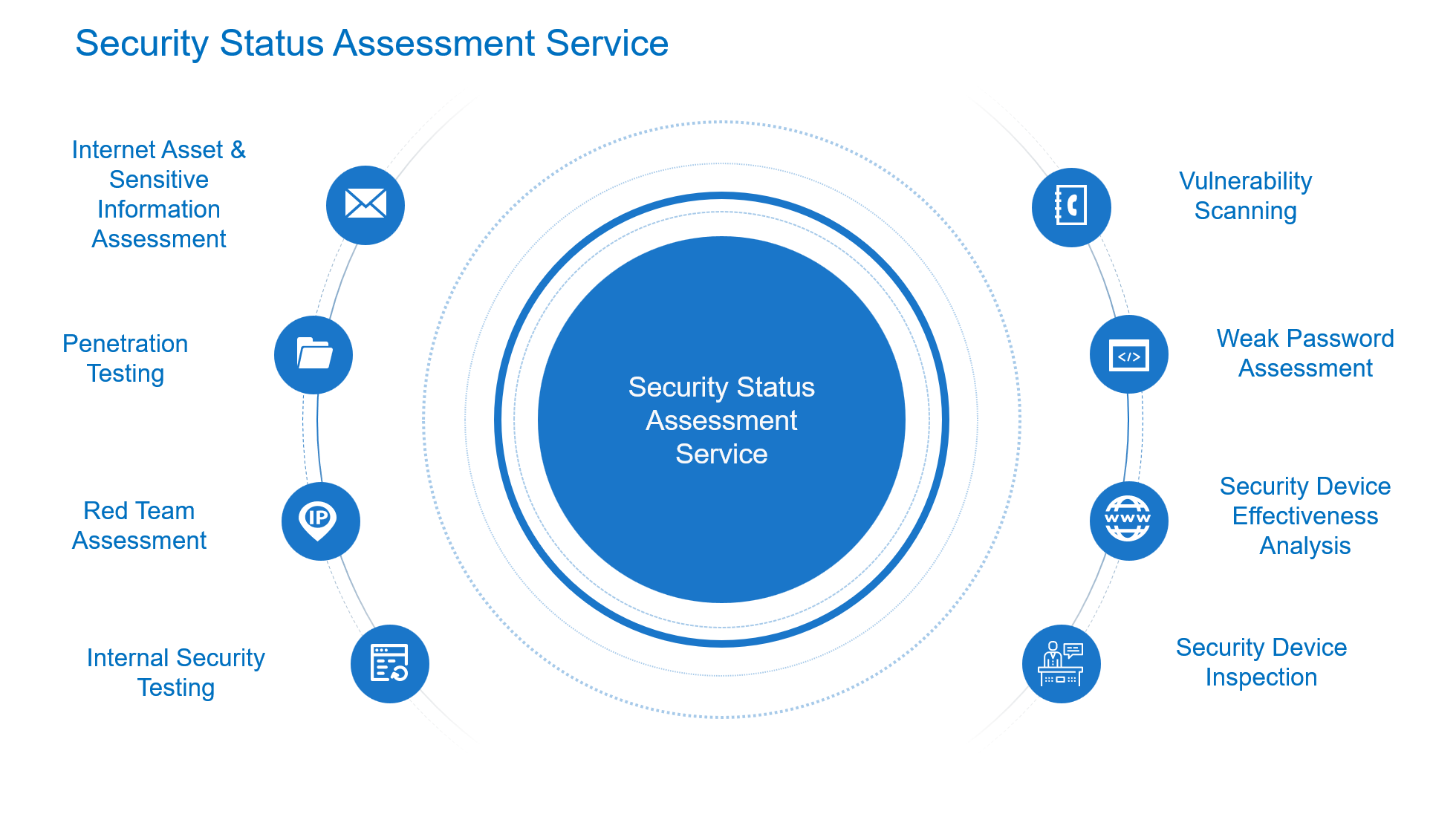
Security Status Assessment Service
A multi-dimensional security audit service that identifies risks in an organization's cybersecurity framework.
Contact WebRAY
Current Location:
Home
>
Products
>
Security Services
>
Professional Services
>
Security Status Assessment Service
Service Overview
Security Status Assessment Service builds on traditional penetration testing by collecting an organization's internet-exposed assets and sensitive information. It employs deep and basic penetration tests, vulnerability scanning, and supply chain testing to simulate attacks aimed at obtaining internal access or sensitive data. Combined with multi-dimensional internal security checks, including network architecture analysis, core business configuration review, and endpoint security testing, the service identifies gaps and vulnerabilities in the organization’s cybersecurity posture.
Service Advantages
-
 Professional Team
Professional TeamOur security team consists of senior cybersecurity experts with extensive experience in red teaming and incident response. Having won multiple awards in security drills and competitions, we offer professional technical support and capability assurance.
-
 Comprehensive Coverage
Comprehensive CoverageThe service covers all aspects of the enterprise network environment, ensuring complete protection.
-
 Diverse Products
Diverse ProductsFocusing on vulnerability detection, application security defense, traceability management, and cyber mapping, we are dedicated to analyzing the digital world from a cyberspace perspective and creating a comprehensive cyber map.
Application Value
Comprehensive Testing
Conducting thorough security analysis through basic penetration testing, vulnerability scanning, supply chain testing, and social engineering tests, combined with internal network architecture security analysis, core business configuration checks, and endpoint security assessments.
In-depth Testing
Conduct thorough security assessments targeting an organization's internal cybersecurity infrastructure to gain access to internal privileges or sensitive data. This enables comprehensive analysis of attack paths and addresses gaps in security development.
Real-world Testing
Red team security testing based on realistic attack-and-defense scenarios, closely aligned with actual production environments. This provides a clearer understanding of the current cybersecurity posture.